Cybersecurity Awareness Month: The SaaS Vulnerabilities You Can’t Ignore
Since a presidential and congressional decree in 2004, October has been observed as Cybersecurity Awareness Month. The focus of this awareness month is to promote action and conversation around the safety and security of our ever-evolving digital world.
The proliferation of cyberattacks is expected to majorly impact business and the economy. Some estimates suggest that the cost of damage resulting from cybercrimes will grow exponentially to account for nearly $10.5 trillion by 2025. That means that organizations must take a hard look at their current cybersecurity practices and determine every area of vulnerability within their digital ecosystems.
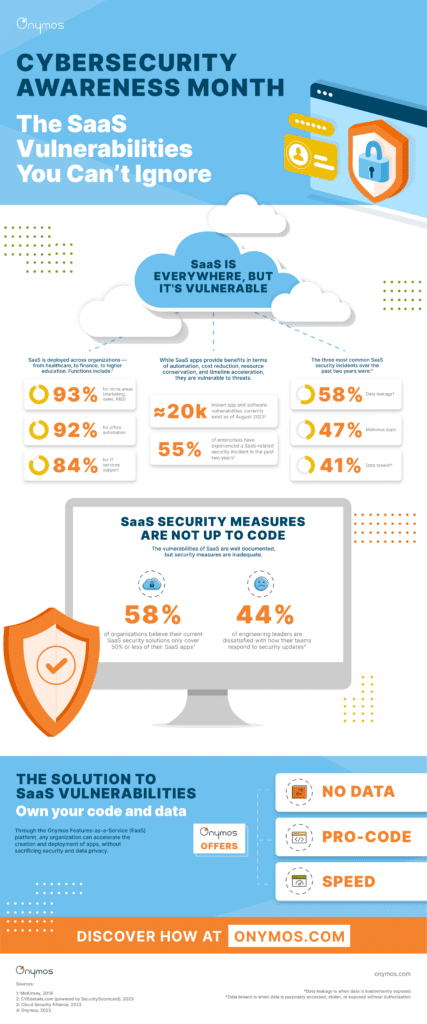
One of the largest — but least obvious — vulnerabilities most organizations have today is their own third-party software-as-a-service (SaaS) integrations.
Every sector, including government, healthcare, education, finance, and utilities, relies on a complex web of SaaS integrations. These organizations often deploy it to simplify or streamline IT, marketing, sales, and administrative activities.
While SaaS offers many benefits to these organizations, it is extremely susceptible to cyberattacks for one major reason: its access to data.
SaaS Has Data, Making It a Critical Target
Data access and privacy have been a key topic of discussion over the last few months because of Zoom. The video software giant’s broad access to customer data was recently brought to light. Even though this news was not associated with cybercriminal activity, it should set off alarm bells about how much access SaaS providers have to data. Almost every organization today shares control of its company and customer data across dozens of third-party vendors.
Onymos Founder and CEO Shiva Nathan recently shared his thoughts on the Zoom debacle and the state of SaaS, asserting, “Zoom is the model for what is wrong with SaaS today. They rent your software with their right hand and take your data with their left. SaaS is broken.”
Shiva shared with Cybersecurity Dive, “CIOs have to fundamentally look at the software as a service that the business consumes. In the same way that you look at your security posture, you need to look at your data posture.”
This discussion has only deepened after the recent cyberattacks experienced by top Las Vegas casinos, MGM and Caesars. The attacks are suspected to have been social engineering hacks that compromised third-party software vendors. This resulted in not only data being held hostage but systems and operations too. That is just the beginning of the impact — MGM and Caesars are already facing class-action lawsuits.
The MGM and Caesars attacks are not the only “vendor compromise” hacks we will see this year or in the years to come. More are inevitable because SaaS “vendor compromise” is commonplace.
That’s why it is imperative that CTOs, CIOs, CSOs, and IT teams uncover all of their SaaS vulnerabilities and begin mitigating them immediately.
SaaS Is Broken, But There’s a Solution
Security and access have to be non-negotiable. Organizations shouldn’t have to sacrifice their data, applications, systems, operations, and overall success to the subpar security measures provided by typical SaaS vendors.
That’s why, at Onymos, we believe organizations should own their data and their code. We think every organization should look for vendors that apply this principle.
To learn more about the vulnerabilities of SaaS and how security and data access are handled at Onymos, check out the infographic below.