The HIPAA Compliance Automation Checklist

Healthcare generates enormous amounts of data, zettabytes worth of lab tests, images, sensor readings, prescriptions, and patient histories. On this scale, HIPAA compliance automation isn’t just a convenience or a “nice-to-have.” It’s a necessity.
But not all automation is created equal. If you don’t understand your automation solutions, you could be trading efficiency for risk.
The problem with manual processes
HIPAA requires that patient data be accurate… but if you’re relying too much on manual processes, your data’s integrity is almost certainly in question.
- Hospitals & clinics: Multiple studies have shown that administrative burden is overwhelming caregivers and is associated with clinician errors and burnout. In a survey of three U.S. health systems, about 20% of patients who read their visit notes reported finding errors. 40% said the errors were serious.
- Laboratories: Even the simplest manually managed lab spreadsheets have error rates ranging from 18% to 40%, and complex ones include at least some errors nearly every time. It’s not surprising then that over 50% of pharma and biotech leaders report that “poor-quality, poorly curated datasets” are the biggest barrier to adopting transformative new tech (like AI).
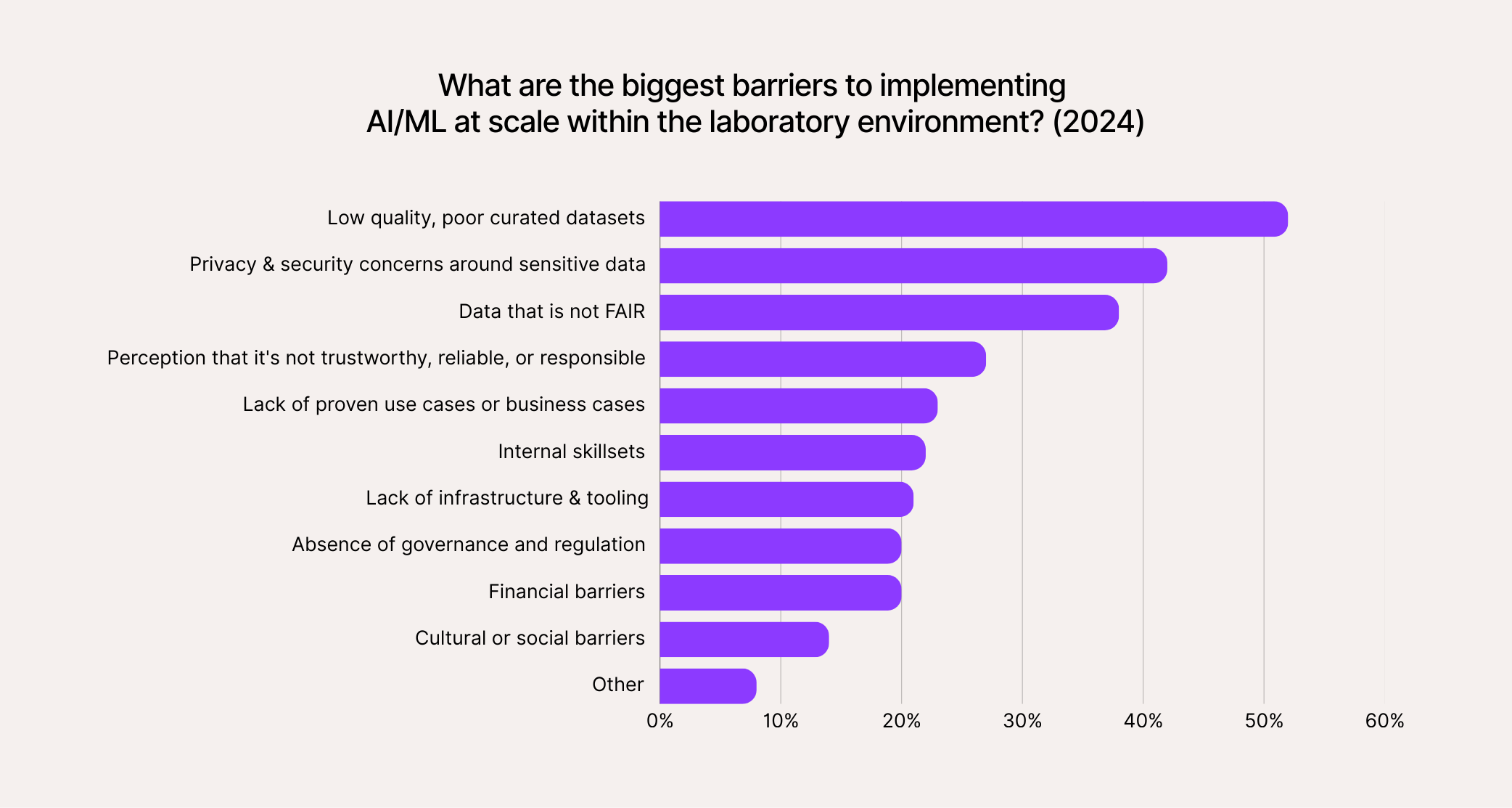
So, healthcare and life sciences may generate a lot of data, but not always good data. Low-quality inputs mean compliance risks, unreliable insights, wasted resources, and potentially even endangering the patients themselves.
With today’s data volumes, manual processes can’t realistically guarantee the integrity of protected health information (PHI). While that doesn’t mean every organization is outright non-compliant, it does mean most are falling short of HIPAA’s intent.
The ROI of compliance automation in healthcare
Too many organizations see “compliance” as overhead, something necessary for keeping patients and their PHI safe. But done right, with automation, HIPAA compliance generates real ROI and helps you create high-quality, well-curated datasets.
Take the problem of duplicate entries in electronic health record (EHR) systems. Some hospitals and clinics report that up to 30% of these entries are actually duplicates. Each one undermines the data integrity of the whole system and, practically speaking, makes it harder for caregivers to find the right information when they need it.
Intermountain Healthcare introduced an automated patient-matching system to solve that problem. By automatically comparing demographic details and spotting likely matches, the system reduced duplicate patient creation by more than 30% in its first six months.
The same study highlights that manually fixing each of those duplicate errors costs approximately $60. From there, we can extrapolate and find that automation likely produced at least $2M in savings (using a conservative estimate of one million records and 18% duplication).
That’s not even counting the number of hours staff get back annually by not having to chase down the right data. A similar UK case study found that eliminating and preventing duplicate records saved staff 650 hours.
The difference between automation and automating HIPAA compliance
Imagine an urgent care doctor pastes a patient’s PHI into ChatGPT for analysis with “deep research” enabled. That is automation, outsourcing the work to AI. But the moment PHI leaves the clinic’s secure environment and flows to OpenAI, HIPAA is being violated.
That’s automation creating a compliance risk. Data breaches like this (and this is technically a data breach) are likely happening more than you think (or, maybe they’re happening exactly as much as you think).
Not that you can’t rely on third-party automation software or compliance tools when you do have a business associate agreement (BAA) in place. But be aware of the risks. When you let someone else be responsible for your data, you don’t really know what the outcome will be, even when you’re dealing with “trusted” partners and “secure” platforms.
That’s why HIPAA’s Privacy and Security Rules don’t just emphasize encryption, access controls, and audit trails, but also accountability. They phrase it in regulatory language rather than using the word directly, but make no mistake, if your vendor experiences a data breach or a lapse in security, you’re responsible.
In 2024, over 40% of all reported third-party data breaches occurred in the healthcare space, more than any other industry.
A checklist for auditing potential automation solutions and your org’s readiness
HIPAA’s technical safeguards for electronic protected health information (ePHI) are outlined here. They’re broadly categorized under “access control,” “audit control,” “integrity,” “person or entity authentication,” and “transmission security.”
✅ Who controls the data, and how is the software deployed?
A true HIPAA compliance automation solution gives you control over your own data. That means flexible deployment options inside your environment, whether on-premises or within your cloud tenancy, and a design that keeps the vendor out of your data stream.
If the software requires sending PHI to a third party for processing, you’re exposing yourself to risk. Be sure that you thoroughly understand their data retention and secure deletion policies.
The best solutions should encourage data sovereignty, not undermine it. They might leverage emerging data control models like decentralized federated learning (a technology that allows AI models to be trained across multiple data sources without those sources sharing their raw data with each other), VPC processing (computing that happens inside a virtual private cloud), or No-Data Architecture (software architected and optimized to run inside a customer’s infrastructure without needing to transfer data outside of it).
✅ Does the automation improve data integrity?
It’s important to distinguish between process automation and data integrity automation. They can be the same thing, but they don’t have to be the same thing. A laboratory robot might speed up testing by automating sample prep, but it doesn’t necessarily make your data cleaner or more trustworthy.
Other kinds of automation, like check-in kiosks or report generation tools, may even exacerbate issues if they rely on (or allow users to input) bad data. In fact, this is why many AI initiatives fail. Forbes says what sets companies that are successful at implementing AI apart is that they see AI projects “as data projects, or sometimes even data products.”
If a tool only speeds things up without making the underlying data more trustworthy, it’s not HIPAA compliance automation. It’s garbage-in, garbage-out, just faster.
✅ Can the system stand up to an audit?
Most modern enterprise-grade automation solutions highlight logging and reporting as core features. In practice, there are still gaps, especially when tools are repurposed for healthcare without being built for HIPAA from the ground up. For example, UiPath, a robotic process automation (RPA) platform, touts its built-in logging capabilities, but it’s not as simple as just “turning them on.”
The UiPath Marketplace, a catalog of UiPath-compatible software components, includes unofficial “add-ons” like the PrimedLogging Enterprise Library.
In a community blog, its developer described the problem he faced: “There was genuine concern when I automated a couple of internal business processes that involved our internal ticketing system and ‘sensitive’ human resources (HR)-related activities. The concern was related to what information is logged by the robot when it was finally deployed to UiPath Orchestrator.”
If your team has the technical know-how, maybe writing your own software to fill in the gaps is workable. But if they don’t, you may have to hire consultants or rely on ad-hoc solutions that the primary vendor does not guarantee. In this case, UiPath’s official policy makes it clear that they do not take responsibility for problems that may arise from using software like PrimedLogging.
FAQ
Get fast answers to your other questions about HIPAA compliance and automation below. Then, reach out to the Onymos team. We’ll show you how DocKnow, our intelligent document and data processing platform, helps healthcare and life sciences organizations automate sensitive workflows without ever compromising HIPAA compliance.